The Hacks Behind Cracking, Part 1: How to Bypass Software Registration
In the event that you've at any point thought about how programming privateers can take programming and break it over and over, even with security set up, this little arrangement is for you. Indeed, even with the present most developed techniques for overcoming robbery set up, it is still moderately simple to split any program on the planet. This is predominantly because of PC procedures' capacity to be totally controlled by a get together debugger. Utilizing this, you can totally sidestep the enrollment procedure by influencing it to skirt the application's key code confirmation process without utilizing a legitimate key. This works since gathering enables you to talk straightforwardly to the processor and power a skirt the enlistment procedure.
In this Null Byte, we should go over how breaking could function by and by taking a gander at an illustration program (a program that fills no need other than for me to hack). I won't walk you through how to really split a honest to goodness program, since I can't simply break a program for show, yet the strategies connected to my illustrations should give you the establishment expected to make your own. By then, it's a trial of your ethics in the event that you need to utilize your insight for good or awful.
Necessities
Windows (for cases just, debuggers exist crosswise over stages)
A debugger introduced: IDA, ollydbg, and so on (ollydbg will be utilized as a part of illustrations)
Stage 1 Test the Program
To begin with, run the program that you are endeavoring to figure out and attempt to initiate it with an irregular key to confirm that you require a substantial programming key to continue. This is to check that we can concoct the keys.
Stage 2 Run the Program in a Debugger
- Run ollydbg
- Open up the program you wish to sidestep with ollydbg.
- Tap the play catch to run the program with the debugger appended.
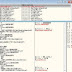
- Right tap the CPU window, and snap Search For > All intermodular calls.
- Look for high intrigue DLLs. GETDLGITEMTEXT, will be for exchange boxes, which get called when you attempt to enter a product key. By venturing into the capacity with the debugger, we can analyze the enlistment particularly. SENDDLGITEM could be utilized also.
7. Resume the program and enter any product key you feel like. In the event that the debugger breaks (stops the program's execution) subsequent to entering your key, at that point you know you discovered DLL in stage 5.
8. Press F8 back in the CPU window to compel the following stage until the point when you get to the TEST EAX. EAX is the arrival of an esteem, which implies that a check is being performed here. Upon examination, we can see that the EAX is checking for a number that isn't equivalent to an invalid esteem. This implies in the event that it is supplanted with something besides invalid, it will run.




0 comments:
Post a Comment